BLOG
We work passionately to change the future with our young, dynamic, and creative team
Reycan Çetin // Growth Manager @Techsign
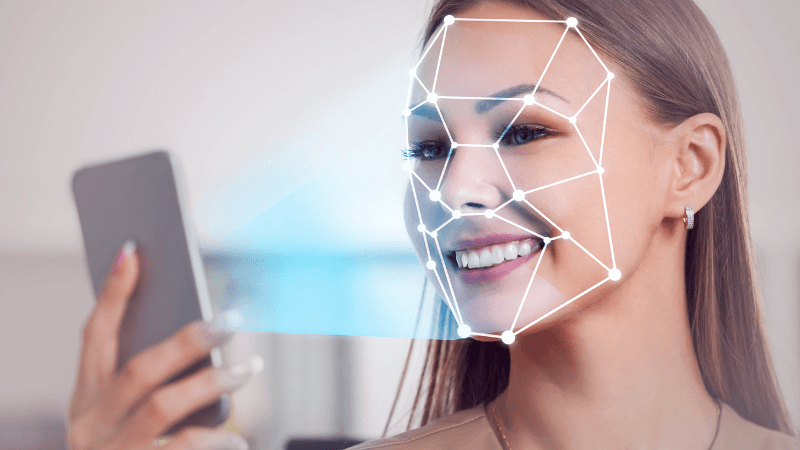
Contactless payment systems became more and more popular after Covid 19 pandemic. Contactless payment systems provide great advantages for both healthcare and user experience. There are many contactless payment methods, and pay-by-face is one of the newest.
This new method is called pay-by-face or facial recognition payment. You can easily understand by just looking at the name, the system lets users make payments by introducing their faces. So the users don't need to carry cash, credit/debit card, or even cellphone. With these features, pay-by-face is a fast, easy, and secure payment system. It is secure, yet to get the payment the user's face must be recognized. And people can steal your id card, cellphone, or id card number, but not your face! Of course, your technology must be good enough to separate a photograph from a real person's face. We will talk about the technology below, how it works, what points should be considered, etc...
What are the use case scenarios for PBF?
Pay by face can be theoretically used instead of credit cards in all areas. Physical shops, online shopping, self-service food courts, taxis, public transportation, etc... In all these areas, users already pay with other contactless methods. For example, we pay through applications in taxis, we use QR codes in public transportation, and we pay through our smartwatch by using NFC. But all these transactions have something in common. They all depended on a device. If the smartwatch's battery dies or the credit card is forgotten, the user can not pay. Pay by face puts an end to all these problems. Because your face can not be stolen by someone else, and also can not be forgotten by you!
China uses PBF very actively, experiencing covid 19 horribly many habits had to change in China. One of them is the payment systems. China left to use cash in many areas. Different than Europe, many physical shops even don't accept cash, only mobile payments. Almost all physical shops provide a QR code payment option. But recently PBF is getting more and more popular. With the PBF option, users don't need to open their wallets, or even use their cell phones. It is really a good time saving for China's crowded cities.
Besides China, Russia uses PBF actively too. In 2021 Moscow Subway started to use Face Pay to provide passengers facial payment. It is the first time a public transportation system uses pay by face. Moscow Subway is one of the most crowded subways in the world, and authorities say that it saves a lot of time. PBF devices are on 240 stations, and the passengers use them voluntarily. They can still use passenger cards. If the passengers prefer to use PBF, they download the app and introduce their face and preferred card. That's all.
Advantages of Pay by Face
It is accepted that contactless payment systems are crucial for public health. Nowadays more and more sectors use contactless payments such as contactless credit cards, QR code payments, payment with NFC, etc... Pay by face offers many advantages when it was compared with other methods.
1. Unstealable, unforgettable, unlosable biometric features
As I mentioned before, the biggest advantage of PBF is being independent on any device. If someone steals your contactless credit card, the thief can use it before you beware and cancel the card. It is similar to QR code payment if someone steals your phone.
Being dependent on a device creates a problem when the user forgets the device too. Forgetting the card/cellphone/smartwatch is not a problem with PBF. It is secure and also provides a better user experience.
2. Time-saving
PBF saves a huge amount of time in busy places such as public transportation stations, self-service restaurants, big shops, etc...
You can watch the Moscow subway's face pay by clicking the link.
3. Identity verification with low error rates
Face recognition verifies identities with high technology. It can easily adapt the changes such as glasses, masks, make-up, etc...
4. Building customer locality programs
Managing the customer subscription system is easy with PBF. Customers don't need the enter their subscription number every time, and it will be easy to give awards to customers for brand loyalty. It is easy and practical.
Disadvantages of Pay by Face
PBF has no disadvantages technologically, but there is a huge obstacle in front of its spreading. The worries about the security of personal data. Users have concerns about their personal data being kept in the cloud. They think that malicious users can steal data and misuse them. This concern is mostly caused by a lack of knowledge. Users, I mean potential users, think that the system keeps the image of their whole face. And this image can be carried. But actually, face recognition technology develops by eliminating all these risks.
Learning about the technology will help to reduce these concerns. And I want to help, so I will explain the employed technology by selecting simple terms. But first, I want to talk about user experience.
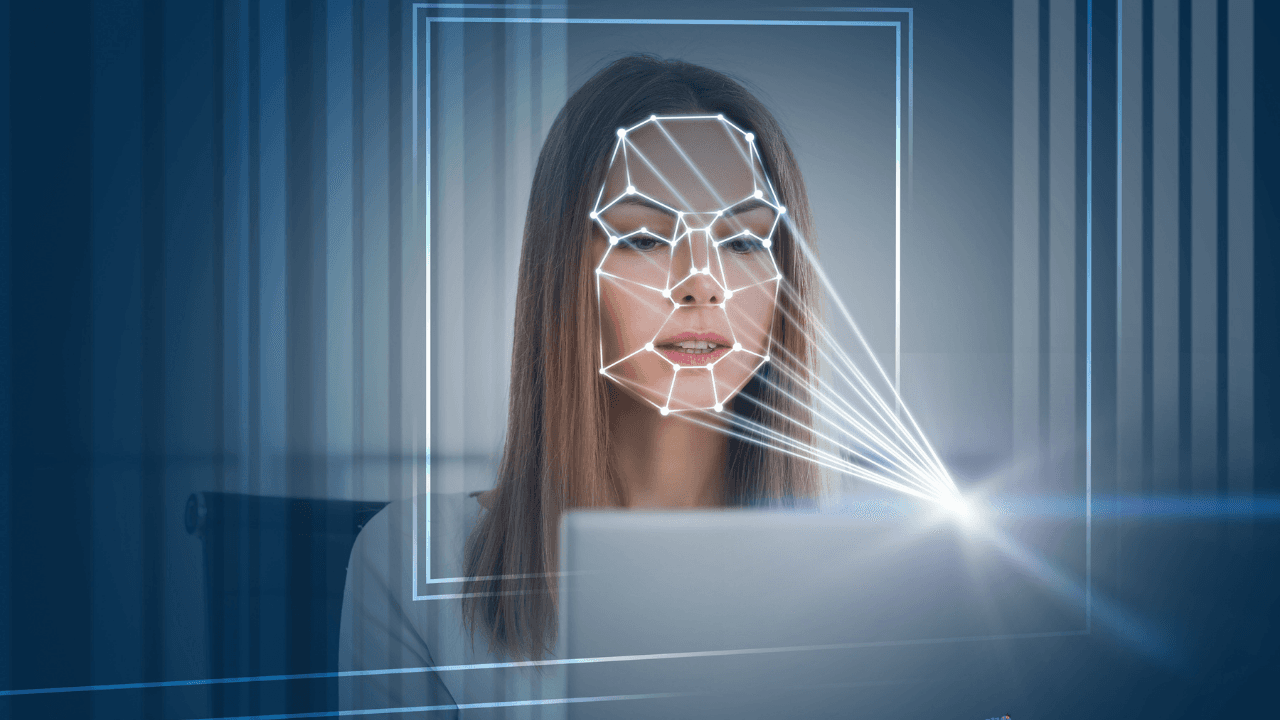
The Steps of Pay-by-Face
User experiences differ a little bit across sectors. But there are two main steps: enrolling the face and using the face for the payment.
In the enrollment process, the users add their needed data which was shaped by the vendor, into the system. They can be email addresses, phone numbers, credit card numbers, etc... And then the users introduce their faces to be added to this newly created account. The system keeps the given data and also, the biometric features of the introduced face. In the payment step, the system recognizes the face and uses this recognized face's data to take payment
What kind of technology is employed in PBF?
Let's start with the most important question that users have in mind: "Can my facial image be transferred elsewhere?" Before diving into the details of the technology, let me answer that right away: NO! Actually, I don't think that it is a paranoid thought. Especially, when I think about the advancements in deepfake technology. This technology can manipulate images and videos by using a target person's face and voice. And it is a big threat. You are right to be concerned. But therefore, it is really crucial to understand how face recognition technology works and how it keeps personal information safe. I'll try to explain it very simply.
First of all, it's worth mentioning that I'm discussing this within the context of face payment systems, but the same principles apply to any facial recognition system.
In face recognitional payment systems, facial data is processed in two stages: during enrollment and during verification.
During the enrollment stage, when a user registers their face, the system creates and stores data based on biometric features. It doesn't store the entire image of the visage. But rather it creates numerical data which is derived from specific biometric features. These biometric features can be the distance between eyebrows, forehead width, cheekbone distance, etc... Only this numerical data is stored on the cloud, not the images of the face. So, even if someone steals these stored data, they can not create a complete face image by using these numeric data.
During the verification stage, the system compares the processed data from the user's biometric features with the stored data. The data being processed and compared are again numerical representations derived from biometric features.
Now, how does the system find the correct person from potentially thousands of registered users for payment? It does so through a mechanism called numerical categorization and indexing.
Let's think of it as searching for a specific book in a library. It is not exactly the same, but it operates on a similar principle. Imagine manually searching for a famous book about deepfake in a library without using any software. We will make choices to narrow our search area. Our book is written by a professional software engineer and has a lot of technical terms in it. So it is obviously not in the children's section. Let's exclude all children's books. Then we can eliminate novels and poetry sections. Step by step, we narrow down our search to non-fiction books. We exclude sports, history, and art books, focusing only on the computer science section. Instead of checking the names of all books in the library, we conduct a detailed search within the narrowed-down area.
Face recognition systems operate similarly. The system compares the numerical data obtained from the user's biometric features by narrowing down the search area. For example, let's assume that the first checked feature is the distance between the nose and chin, and the user's distance is 5 cm. The system excludes all data with distances above 5 cm. This action narrowed down the search area. And the next feature could be face width. If the user's face width is 11 cm, the system finds those with a distance of 5 cm and face width of 11 cm, discarding others. This way, the verification pool significantly narrows down after two or three feature comparisons. Let me remind you again, that these searches are performed based on numerical codes, not the images. And different companies may use different categorization systems. For instance, one company may use a 256-digit code, while another may use a 512-digit code. The representation of the same feature may vary in different digit positions across different coding schemes. Even if one company were to steal another company's data, it would be impossible to interpret and use the code elsewhere.
Let's return to our example. We had assumed that face width was the first feature checked, and it was defined in the 2nd and 3rd digits of a 512-digit code. When conducting the search, the system looks for the numbers that have 1 and 1 in the 2nd and 3rd digits. It keeps the matching numbers and excludes the others. After 2 or 3 searches the area became very small to find the right code. So the system can make the match in just a couple of seconds.

Pay-by-Face by Techsign
Facial recognition payment systems are really common in the Far East but not very well accepted in Europe or USA. And in Turkey, there is no local firm that provides this technology. Oh, there WAS no local firm! As Techsign, we are proud to announce that our Pay-by-face is ready to use! As a short notice, you can see PBF in chain stores, coffee shops, and many other places. Like in all our solutions, we used user-friendly and highly secured technologies in PBF. Our coding system has 512 digits to make it hard to crack it. And our liveness tests success rates are higher than 92%. That means no one can use your picture to make payments from your account.
To get to know better with this technology, please contact us.
SHARE






BLOG