BLOG
We work passionately to change the future with our young, dynamic, and creative team
Identity verification is generally affiliated with the finance sector. However, in reality, our daily lives involve identity verification processes more than we realize. While entering our place with our smart cards, using our smart tickets on public transport, paying with QR codes, etc...
There are a variety of methods for identity verification. Physical devices, passwords, biometric data, etc... However, they all have some disadvantages beyond their advantages. So, what should we do? Cybersecurity experts indicate that we need multi-factor authentication, a combination of at least two different methods.
This view has also been adopted by lawmakers, and many countries' legal regulations regarding remote customer acquisition require this. Especially in the finance sector, the rules are strict and decisive.
In this article, I talked about different authentication methods and tried to explain their advantages and disadvantages. Thus, I want to help companies choose the best methods for multi-factor authentication and inform them about what Techsign offers.

Device Authentication: (Something you own)
As the name suggests, this authentication method requires ownership of a device. Identity verification is done by establishing a physical connection between the device you own and the device you will verify. Smart cards, tokens, and sometimes mobile phones can be used as devices in this method.
This method is low-cost and fast in terms of setup and processing, but physical devices are highly vulnerable to risks such as loss, theft, and forgetting. For this reason, identity verification solely dependent on physical devices is no longer preferred in sectors requiring high security. In fact, we see that alternatives are being sought even in areas that don't need high security, but circulation is intense. More and more countries use facial recognition payment in public transportation and retail stores. Recently, lots of sectors have been reducing Device dependency to increase security and provide a smoother customer experience.
Knowledge-Based Authentication: (Something you know)
KBA is basically based on comparing two answers you gave. The answer you gave at the registration and stored in the database and the one you gave at the login process. Not clear? Let me give a real-life example. System logins that ask for a password for login are an example of this. However, as we explained in our article "Are Our Passwords Secure Enough? What Will Password Usage Be Like in the Future?", knowledge-based authentication has many security vulnerabilities. Passwords can be easily stolen or guessed. Believe me, the majority of people use personal information as passwords because they are easy to remember, For this reason, almost no platform uses this method alone anymore.
Systems also check the device used for login or send an SMS to increase the authentication factor. However, SMS sending is actually another version of device authentication. Mobile devices can also be stolen along with the password.
Biometric Authentication (Something you are)
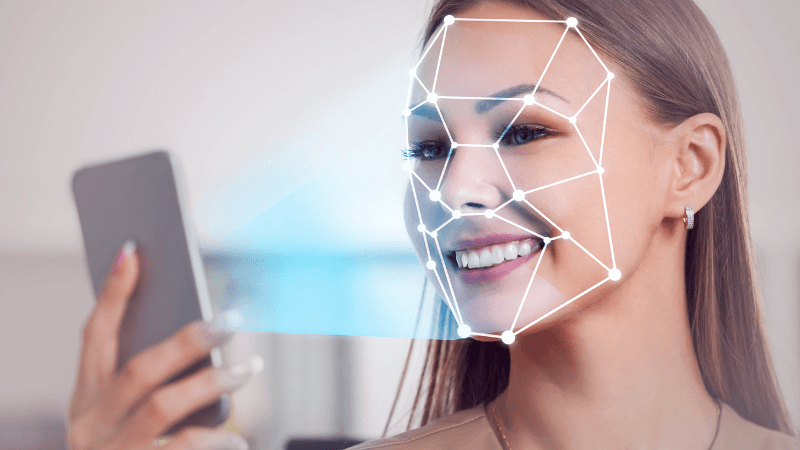
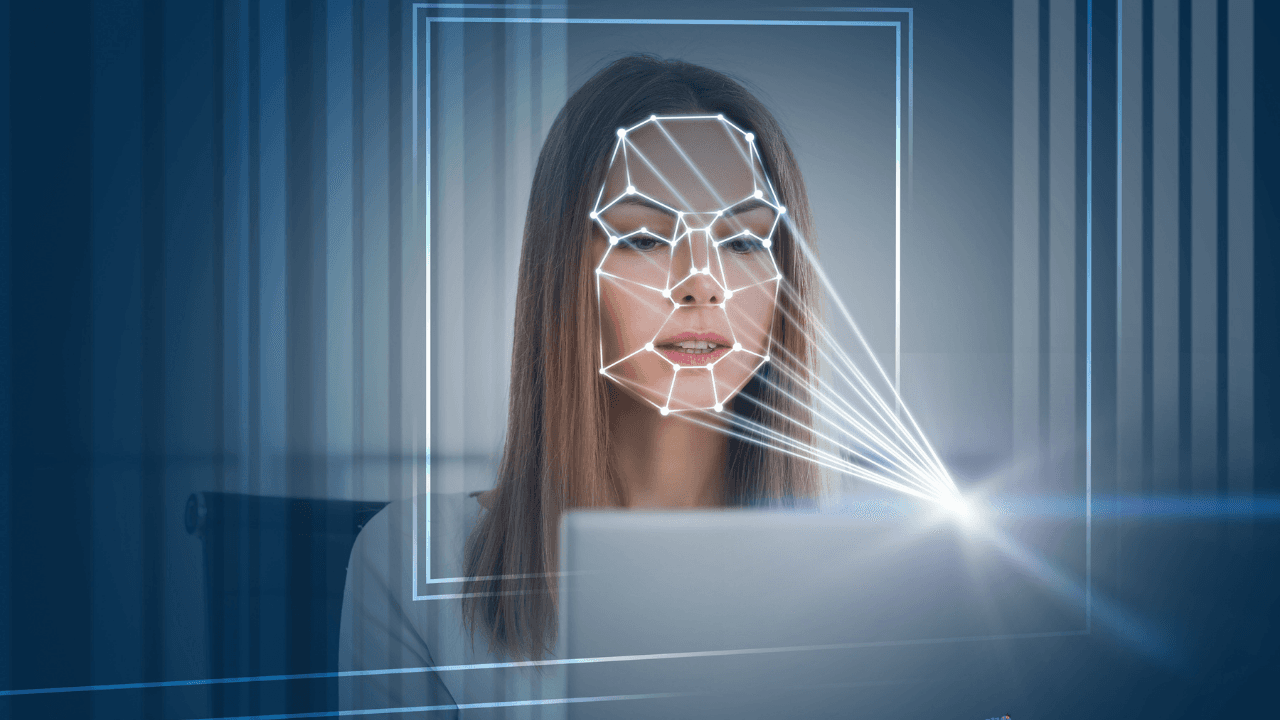
The growing trend for authentication is undoubtedly biometric authentication. Biometric authentication verifies you with something you are, not something you own or know. With your biometric features. Biometric authentication can be done by verifying unique features in a person, such as fingerprint, iris, or voice. However, the most commonly used method is facial recognition due to its convenience. It's not hard to understand that facial recognition is much more practical for users. Think about using your voice in a crowded subway station with all the noises. Or how unhygienic it would be to approach a device for iris authentication.
The biggest disadvantage of biometric authentication used to be its slowness. I say "used to" because, with the development of artificial intelligence, this difficulty has almost completely disappeared. Now, biometric authentication can be performed instantly and with very high success rates.
Location-Based Authentication (Somewhere you are)
Location-based identity verification uses geographic location information to verify a user's identity. The system obtains geographical location information from sources such as GPS, IP address, or GSM cell, processes the location data, and compares the user's common location with the current location. Location-based identity verification can be useful as an additional method to increase security, but it is not very reliable on its own. Detecting natural changes in a user's location is difficult. Additionally, VPN technologies can easily show the device's location in a different place.
Behavior-Based Authentication (Something you do)
Behavior-based identity verification is a method that analyzes a user's normal behavior patterns and habits to verify their identity. This method performs identity verification by using non-biometric data such as a user's keyboard strokes, mouse movements, and touchscreen interactions. Behavior-based authentication contains less personal data compared to biometric authentication and requires less effort from the user since it is based on normal behaviors. However, similar to location-based authentication, detecting natural changes in behavior is difficult, and using this method alone can lead to incorrect results.
Conclusion
When we examine the methods listed above, biometric authentication seems to be at the top of the list. Biometric data is resistant to device-related loss and theft risks and eliminates the risk of forgetting in information-based authentication methods. However, while artificial intelligence technologies make biometric authentication easier, they also open the door for fraudsters. Fraudsters who use AI-based deepfake technology skillfully can also mimic biometric data. So what should be done? The answer is actually quite simple: use multi-factor authentication and get your service from high-technology companies.
Let's elaborate a bit more on these two measures. The first is to authenticate the user's identity using at least two different methods, as emphasized by lawmakers. Adding biometric authentication as one of these methods will increase the security level. Second, regardless of the chosen methods, work with companies that offer the highest technology products in the field. Adding biometric authentication has no meaning if fraudsters can easily surpass facial recognition with a photo.
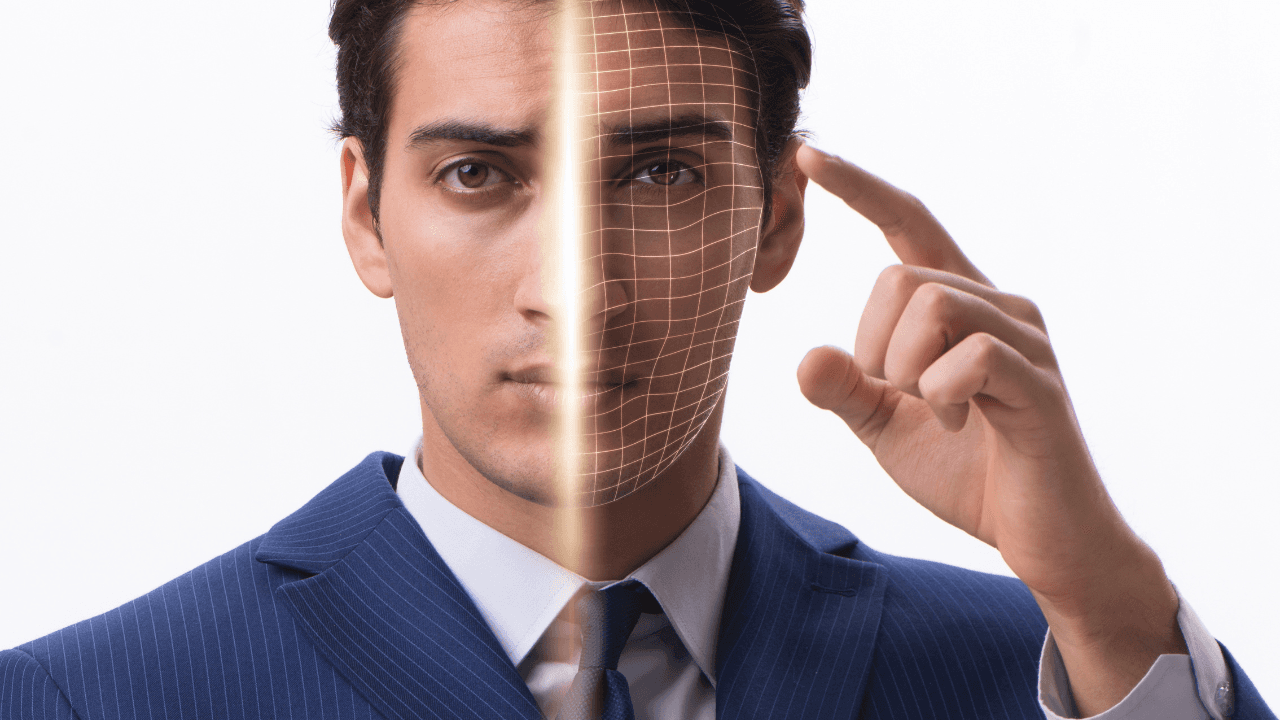
At Techsign, we trust biometric authentication the most as an identity verification method and develop our technology in this area. The success rates of our solutions, which are scored through NIST, are high and satisfactory in this context. However, we closely monitor the fraudsters' development and do not neglect additional security measures. We strengthen our system with additional methods such as tracking and interpreting device and location information and adding SMS OTP when necessary.
To fraud-proof your system easily and securely, contact us now!
info@techsign.com.tr
SHARE






BLOG