BLOG
We work passionately to change the future with our young, dynamic, and creative team
Reycan Çetin // Growth Manager @Techsign
Do you remember our previous article about Deepfake?
Previous article: What is deepfake?
We briefly discussed that Deepfake content is not only a threat to individuals' personal lives, they can also cause social threats and financial crimes.
This time, I'd like to delve a bit deeper into how and why Deepfake is used to deceive financial systems, the measures taken against these threats, and the new methods fraudsters are coming up with in response.
As you can see from the sentence above, there's an ongoing symbiotic relationship between cybersecurity experts and fraudsters. One side is trying to breach security measures, while the other is building impenetrable defenses. In a way, this fight drives technological advancement for both sides.

However, our focus here is not on technological progress but on ensuring the security of financial systems. Therefore, we need to stay one step ahead. Nevertheless, we can't help but appreciate how sophisticated these fraud attempts have become. No worries, we are always one step ahead and don't fall for content generated by Deepfake. Still, I wanted to share how the quality of these attempts has improved and emphasize the importance of working with a reliable identity verification firm.
Fraud Attempts by Using Deepfake
Deepfake-generated content can be used in various ways to attack financial systems. Let's provide examples through a few scenarios:
Ghost Accounts: The first method involves using the personal information of deceased individuals for financial gain. Criminals acquire the victim's information and use it not only to empty their accounts but also to apply for loans, mortgages, or purchase properties and vehicles.
Concealing the Deaths of Loved Ones: Concealing the deaths of family members to gain financial benefits was prevalent even before Deepfake technology. Try searching for "Man receiving his deceased mother's pension" on a search engine, and you'll see cases from around the world. Especially during the COVID era, when masks made identity verification more challenging, this method became more popular among fraudsters. Now, with masks off, Deepfake is the needed tool. The fact that most banking transactions are conducted online has also made it easier for fraudsters
Opening New Accounts with Stolen Identities: One of the most common and widespread forms of fraud, - both for us at Techsign and globally -, is opening new accounts with stolen identities. Here's how it works: the fraudster steals a person's identity card and uses it to open a bank/payment app/money transfer app account. For opening these accounts, security systems ask to see the potential customer's face. It is where fraudsters need Deepfake. They create a picture or video using his picture and pretend the ID card owner.
What harm could someone do by opening an account in your name? Oh, actually it can cause many problems on your behalf. Fraudsters could use this account to finance terrorist activities, send money to gambling and betting sites, and purchase illegal goods and services. In a functioning legal system, it might not result in you being held responsible, but you'll certainly lose time and money, depending on the scale of the crime.
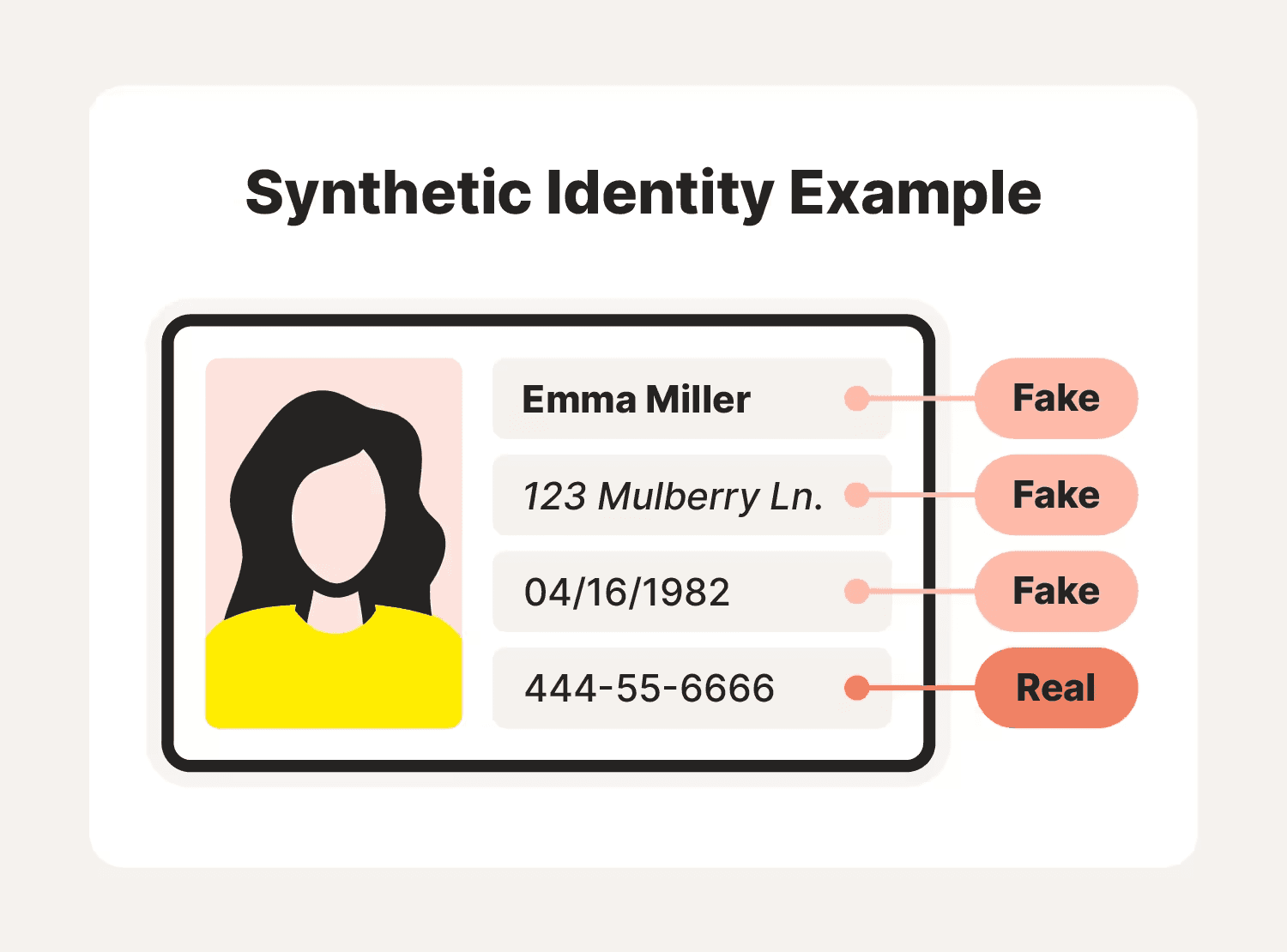
Synthetic Identity Fraud
This type of fraud is not very common in Turkey due to its centralized system. Nevertheless, let me briefly explain how it works. Instead of stealing a real identity, fradsters combine fake, real, and stolen information to create a non-existent person. This fictitious person has an ID with a photo, and an identity number, and also can answer questions while appearing on camera. Fraudsters can apply for credit and bank cards, open accounts, send money - essentially, perform all online banking transactions.
Fraud Attempts that Our Customers Faced
As we've enhanced our security measures, the quality of attack attempts has also improved. But before delving into the details of these attempts, let's discuss a standard new customer acquisition process. This will help illustrate at which stage they attempt to deceive the system.
When a customer wants to open a new account, they first show the front and back of their ID. The system uses OCR to extract information from the ID and checks if the ID number is in the country's database. Then, if the phone has NFC, or if not, it uses Hologram verification to check the authenticity of the ID.
This verification is crucial, because we provide our ID numbers and even photocopies of our ID cards in many places. Turning this information into a convincing ID card that human eyes can't distinguish is not very difficult. So, we perform a chip verification by NFC or hologram check.
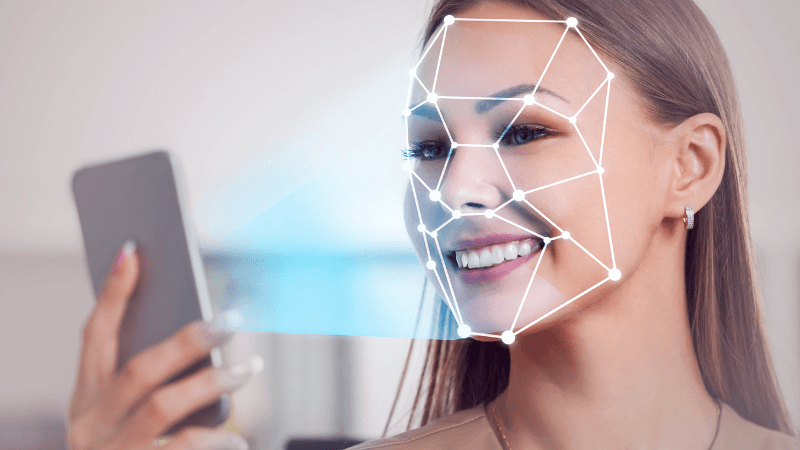
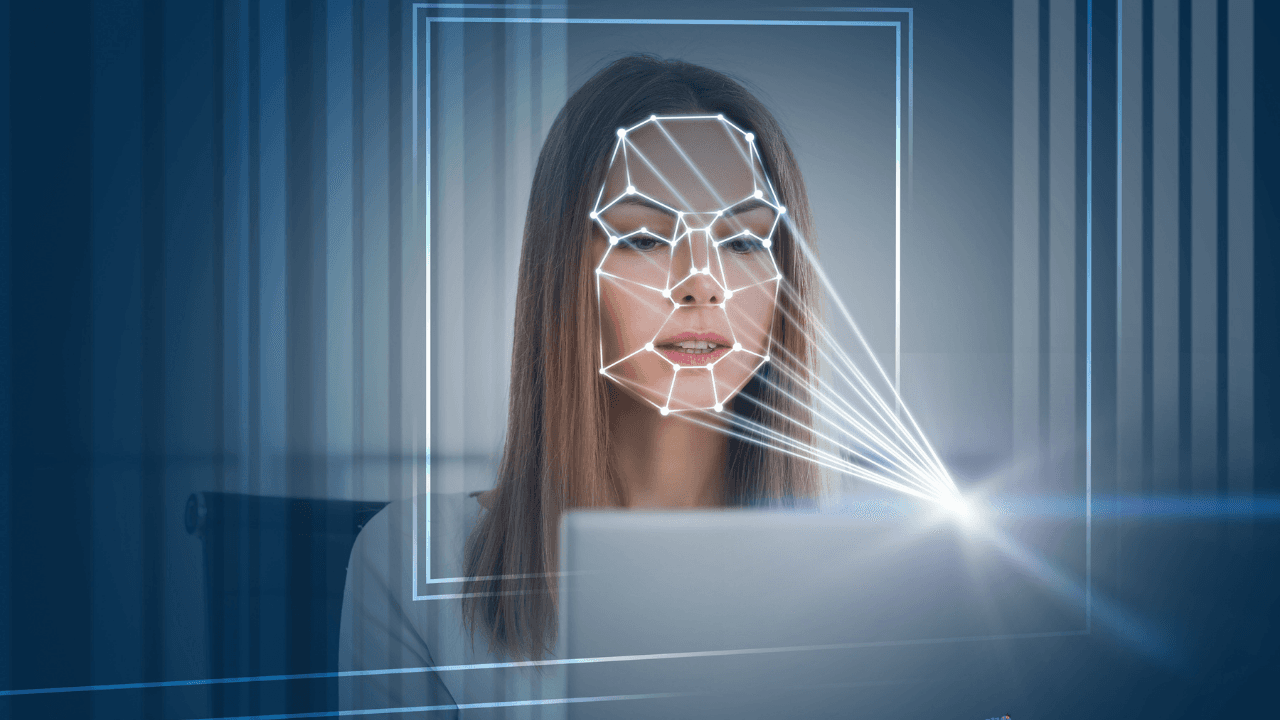
However, these checks cannot determine if the ID is stolen. That's why we need facial recognition and a liveness test.
At this stage, the system asks the account applicant to show their face to the front camera to verify if they are the actual owner of the ID card. Checking if the faces (picture on the ID card and introduced face) match is the first step. The second step is ensuring that it is a real person. The system asks to applicant to turn his head or blink. This is where fraudsters turn to Deepfake to bypass this stage.
Primitive Deepfake Attempts
Techsign's KYC solutions verify about 20000 user identities per day and it was 10.000 last year. And as much as the numbers increased, we've encountered more sophisticated fraud attempts. In 2022, fraudsters didn't take our protection methods too seriously. We saw attempts where they enlarged the photo of the person on the stolen ID and rotated it to mimic the required movements for the liveness test. Yes, exactly like that.
Aging Effects
Over time, these attempts have become more professional. Some of the attacks, at least to the human eye, have become quite convincing. One of my favorite methods is young individuals' attempts. They try to open accounts with the IDs of their parents or grandparents. They use face-changing apps to make themselves appear older and try to deceive the system. In some cases, the results are surprisingly convincing. Due to the relatively low quality of photos on IDs, the human eye might mistake these Deepfake-generated images for the real person. However, detecting this kind of content isn't so challenging for artificial intelligence. Unlike the human eye, AI doesn't consider the face as a whole and doesn't rely solely on visual similarity. It creates biometric data from both photos—the ID photo and the one taken with the front camera—digitizes this data and compares them. In other words, it conducts a much more detailed analysis than the human eye.

Professional Deepfake Content
Recently, the attacks we've encountered have become highly specialized. Fraudsters have gone to great lengths to steal identities and even obtain high-resolution images from NFC to match the ID photo. They use Deepfake to attempt the required movements (head-turning, blinking) for the liveness test in the system. The following video is produced by our team to match the quality of Deepfake examples we've encountered. Doesn't it show a tremendous difference compared to the early attempts? By implementing robust security measures, we're pushing those trying to deceive our system to improve themselves.
In Conclusion
Deepfake is a significant threat that should not be taken lightly. It started to have fun but has evolved into a technology that poses a real danger to financial systems. Moreover, this technology continues to advance alongside improved security measures. Therefore, rather than viewing it as a simple crime to solve and forget about, we must consider it a persistent adversary that requires continuous monitoring and the development of new countermeasures. Techsign is doing its part in this field! We're strengthening both facial verification and liveness tests, and subjecting them to NIST scoring to stay ahead of emerging attacks.
SHARE






BLOG