BLOG
We work passionately to change the future with our young, dynamic, and creative team
Barış Korkmaz
In the digital world, our most valuable assets are our passwords. We use these passwords to access platforms where our data is stored, allowing us to safeguard our information. In this sense, our passwords serve as our most crucial shields.
But how secure are the passwords we create and use? In a world where all aspects of our lives have a digital presence, can others gain access to our passwords or easily decipher them? How can we create more secure passwords? What are the latest trends in ensuring cybersecurity? This content seeks to answer these questions.

30% of internet users experience data breaches due to weak passwords!
Even though many platforms prompt users to create strong passwords, users often use weak passwords by circumventing the algorithms. About 30% of data breaches actually stem from this problem. Malicious users can identify weak passwords easily.
You may be interested: Difference between AML and KYC
13% of users use the same passwords across all platforms
Creating and remembering different passwords for each online platform can be challenging. As a result, many users resort to using the same passwords across multiple platforms. However, this practice can lead to security vulnerabilities. According to statistics, 13% of internet users in the United States use the same password for all their accounts.
Users don't like to change passwords
Another issue is the infrequent changing of passwords. Most users don't change their passwords unless platforms make it mandatory. However, users also have valid reasons for this behavior. Constantly changing passwords, especially for multiple platforms, can be quite cumbersome. Isn't it odd to tape your updated passwords on your refrigerator in this digital age?
Most Commonly Used Passwords
You won't believe it, but according to a study analyzing 15 billion passwords, the top 10 most commonly used passwords are still as follows:
123456
123456789
qwerty
password
12345
qwerty123
1q2w3e
12345678
111111
1234567890
Not too hard to guess, is it?
Many passwords consist of birthdays and names
To make passwords easy to remember, internet users often continue to use birthdays and names. 59% of users create passwords based on names or birthdays. 33% use their pets' names, while 14% use their children's names as passwords. Considering the information we share on social media, accessing birth dates and names is child's play!
A tip for scammers: if the child's name doesn't work, try the grandchildren's name. Given the prominence of grandchild names among the boomer generation, it will work 99%!

Multi-factor authentication
It's been a widely recognized fact for a long time that passwords consisting of letters and numbers alone are not enough. Therefore, multi-factor authentication has been implemented almost since the inception of passwords. Do you remember the security questions like "What is the name of your first pet?" or "What is the name of your elementary school teacher?" when you forget your password? The answers to these questions have become relatively easy to access. Consequently, knowledge-based authentication is gradually becoming obsolete.
You may be interested: What is pay by face?
The use of SMS verification
In addition to knowledge-based authentication, adding supplementary verification methods has become common practice. Especially when a user wants to access his accounts from different devices, usage of these methods becomes even more crucial. Generally, websites perform two-factor authentication by sending an SMS to the registered phone number. However, we can't claim that this method is entirely secure either. After all, who can guarantee that the phone receiving the SMS won't be stolen?
The password management market will reach 3 billion dollars in 2027 With the growing importance of password management, the cybersecurity market in this domain continues to expand. The market's annual growth rate is 20.7%, and the rate of growth is expected to increase.
Biometric authentication is the most secure form of identity verification!
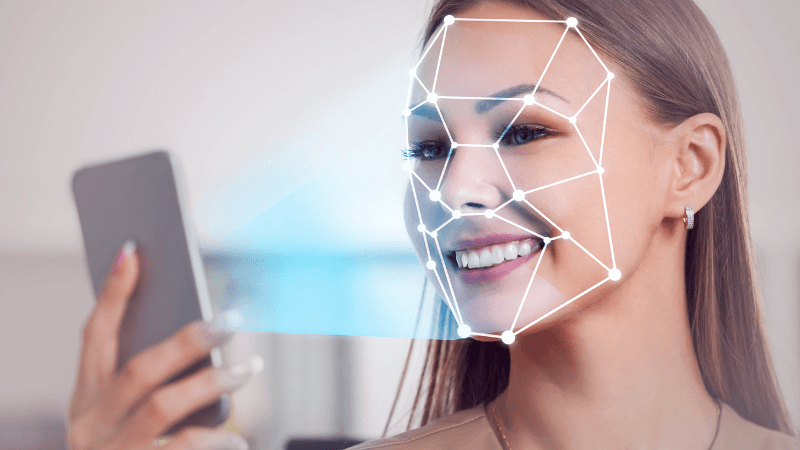
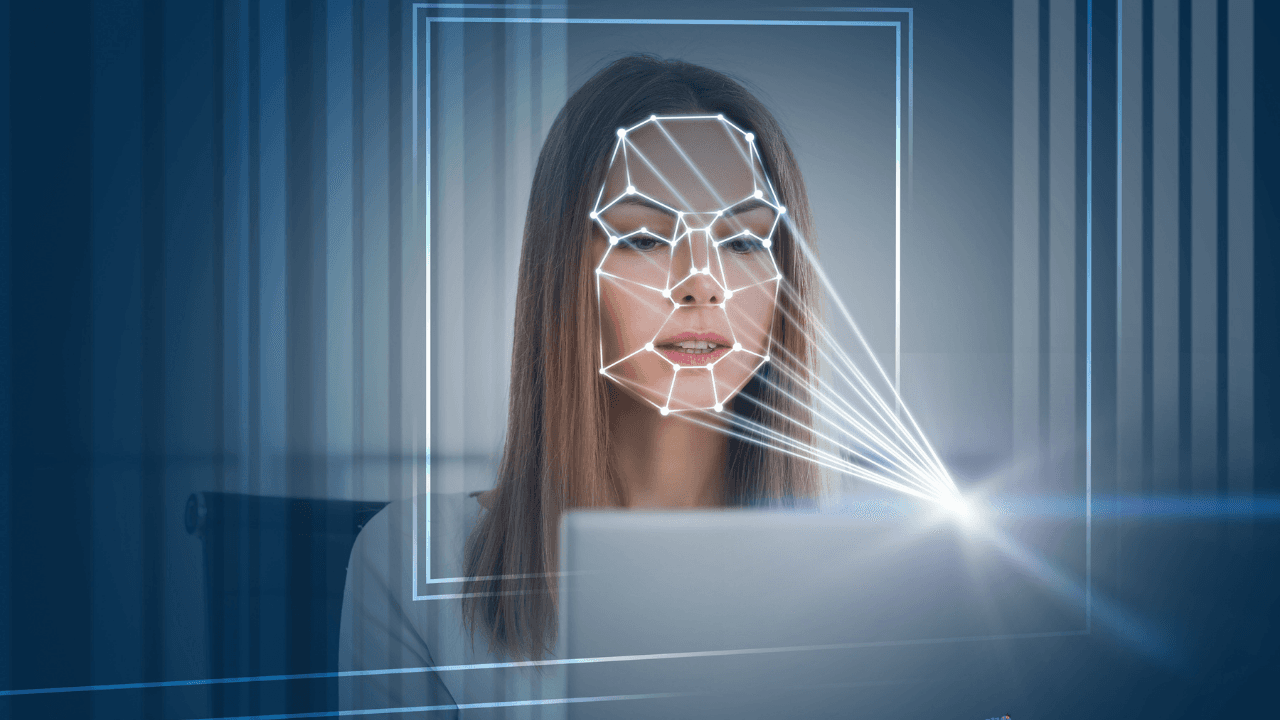
Remote Know Your Customer (KYC) verification gained unprecedented importance during the 2019 COVID-19 pandemic. Processes in various sectors, from finance to education, shifted to remote operations. This practice has become a permanent fixture in virtually every society, even after the end of the pandemic. Experience gained since those days has shown that biometric verification is the most secure form of identity verification. Biometric data cannot be forgotten, imitated, or stolen. There are multiple ways to perform biometric verification, such as fingerprint, iris, and voice recognition, but facial recognition is the most commonly used. After all, we've all learned how to take a selfie on our smartphones, right?
During facial recognition, a liveliness test is also required. Malicious users might attempt to use photos or videos for accounts they don't own. The liveliness test is created to prevent this. Directives like "turn your head to the right, now to the left, blink your eyes, come a bit closer" can be somewhat annoying, but they are necessary to detect videos produced with deepfake technology.
Why is Techsign the right solution for identity verification?
There seems to be a misconception that verifying a customer's identity is only a concern for the financial sector. However, the risk of password theft exists for any platform that requires a password for entry. This implies that secure identity verification systems are needed across all industries.
So why should you trust Techsign for your identity verification processes? Techsign is the company with the highest number of facial recognition transactions in Turkey. A higher transaction volume means that artificial intelligence detecting fraud encounters a broader range of fraudulent techniques, leading to better training and higher success rates. Techsign's facial recognition score above 99.5% confirms this.
Working with Turkey's pioneering companies, Techsign is well-versed in the country's and the world's sectoral needs and legal requirements. As a result, they can assist in designing solutions tailored to their customers' needs.
Techsign solutions can be customized to match customer requirements. This feature allows customers to purchase only the modules they need, preventing them from burdening themselves with unnecessary financial costs.
If you want to enhance your customers' account security and provide better experiences, contact us now!
SHARE






BLOG