Blue Tick for the
Real World!
Blue Tick for the
Real World!
Blue Tick for the
Real World!
Future-Proof Your Business with Secure Digital Solutions!
Onboard customers, verify their identities, and collect their consents. Manage all these processes securely online!
Future-Proof Your Business with Secure Digital Solutions!
Onboard customers, verify their identities, and collect their consents. Manage all these processes securely online!
Onboard customers, verify their identities, and collect their consents. Manage all these processes securely online!









Trust Comes
Before Sales
Güven
Satıştan Önce Gelir
Your Safety
Our Priority
Güvenliğiniz Önceliğimiz
Flexible Infrastructure for Every Environment
Her Ortama Uyumlu
Esnek Altyapı
Scalable Architecture
for
Growing Businesses
Büyüyen İşletmeler İçin
Ölçeklenebilir Mimari
Farklılaşan İhtiyaçlar İçin Bireyselleştirilmiş Çözümler
Flexible and Tailored Solutions for Unique Needs
On-Premises
or
Cloud-Based
Kendi Ağınızda
ya da
Bulut Üzerinde
Her Adımda Uzman Desteği
Expert Support at Every Step
Driven by
Next-Generation Technologies
En Yeni Teknolojilerle Donatılmış
İnovasyon Herşeyin Kalbinde
Innovation at Our Core
Why should you
choose Techsign?
Neden Techsign?
Back
Geri
Forward
İleri
Trust Comes
Before Sales
Güven
Satıştan Önce Gelir
Your Safety
Our Priority
Güvenliğiniz Önceliğimiz
Flexible Infrastructure for Every Environment
Her Ortama Uyumlu
Esnek Altyapı
Scalable Architecture
for
Growing Businesses
Büyüyen İşletmeler İçin
Ölçeklenebilir Mimari
Farklılaşan İhtiyaçlar İçin Bireyselleştirilmiş Çözümler
Flexible and Tailored Solutions for Unique Needs
On-Premises
or
Cloud-Based
Kendi Ağınızda
ya da
Bulut Üzerinde
Her Adımda Uzman Desteği
Expert Support at Every Step
Driven by
Next-Generation Technologies
En Yeni Teknolojilerle Donatılmış
İnovasyon Herşeyin Kalbinde
Innovation at Our Core
Why should you
choose Techsign?
Neden Techsign?
Back
Geri
Forward
İleri
Trust Comes
Before Sales
Güven
Satıştan Önce Gelir
Your Safety
Our Priority
Güvenliğiniz Önceliğimiz
Flexible Infrastructure for Every Environment
Her Ortama Uyumlu
Esnek Altyapı
Scalable Architecture
for
Growing Businesses
Büyüyen İşletmeler İçin
Ölçeklenebilir Mimari
Farklılaşan İhtiyaçlar İçin Bireyselleştirilmiş Çözümler
Flexible and Tailored Solutions for Unique Needs
On-Premises
or
Cloud-Based
Kendi Ağınızda
ya da
Bulut Üzerinde
Her Adımda Uzman Desteği
Expert Support at Every Step
Driven by
Next-Generation Technologies
En Yeni Teknolojilerle Donatılmış
İnovasyon Herşeyin Kalbinde
Innovation at Our Core
Why should you
choose Techsign?
Neden Techsign?
Back
Geri
Forward
İleri
All identity verification solutions you need
Resilliant to AI driven threats
All identity verification solutions
you need
Resilliant to AI driven threats
All identity verification solutions you need
Resilliant to AI driven threats

Kimlik Doğrulama
Risklerinize özel tasarlanan esnek ve güvenli çözümler
Risk skorunuza göre, uçtan uca veya modüler olacak şekilde kimlik doğrulama çözümünüzü sizin için birlikte tasarlayalım.

Kimlik Doğrulama
Risklerinize özel tasarlanan esnek ve güvenli çözümler
Risk skorunuza göre, uçtan uca veya modüler olacak şekilde kimlik doğrulama çözümünüzü sizin için birlikte tasarlayalım.

Kimlik Doğrulama
Risklerinize özel tasarlanan esnek ve güvenli çözümler
Risk skorunuza göre, uçtan uca veya modüler olacak şekilde kimlik doğrulama çözümünüzü sizin için birlikte tasarlayalım.

Alanınıza, ölçeğinize ve bulunduğunuz bölgeye özel çözümler için bizimle iletişime geçin.
İşletmeniz için en
güvenli yolu birlikte keşfediyoruz.
Get in touch to shape custom-built solutions
aligned with your field, scale, and geographic
region.
Together, we discover
the secure path for your
business.

Alanınıza, ölçeğinize ve bulunduğunuz bölgeye özel çözümler için bizimle iletişime geçin.
İşletmeniz için en
güvenli yolu birlikte keşfediyoruz.
Get in touch to shape custom-built solutions
aligned with your field, scale, and geographic
region.
Together, we discover
the secure path for your
business.

Alanınıza, ölçeğinize ve bulunduğunuz bölgeye özel çözümler için bizimle iletişime geçin.
İşletmeniz için en
güvenli yolu birlikte keşfediyoruz.
Get in touch to shape custom-built solutions
aligned with your field, scale, and geographic
region.
Together, we discover
the secure path for your
business.







NFC + OCR
On-device NFC reading with PACE key agreement and Chip Authentication (EAC).
Deep neural network–based AI model for OCR.
Cihaz üzerinde PACE anahtar anlaşması ve Çip Doğrulama (EAC) ile NFC okuma.
OCR için Derin Sinir Ağı tabanlı yapay zeka modeli.
Kimlik Kartında Bütünlük
Rainbow, Guilloché, Gizli Görsel, İmza Karakteri, Hologram, Photoshop Manipülasyonu ve 200’den fazla ek kontrol.
Full ID Card Integrity
Rainbow printing, Guilloché patterns, hidden images, signature character verification, hologram checks, Photoshop manipulation detection, and over 200 additional controls.
Hologram
Akıllı Cihaz İçi Kontrol: Kullanılamaz fotoğraf çekimini otomatik olarak engelleme ve kullanıcıyı en iyi açıyı bulması için yönlendirme
Smart on-device control: automatically preventing unusable photo capture and guiding users to find the optimal angle.
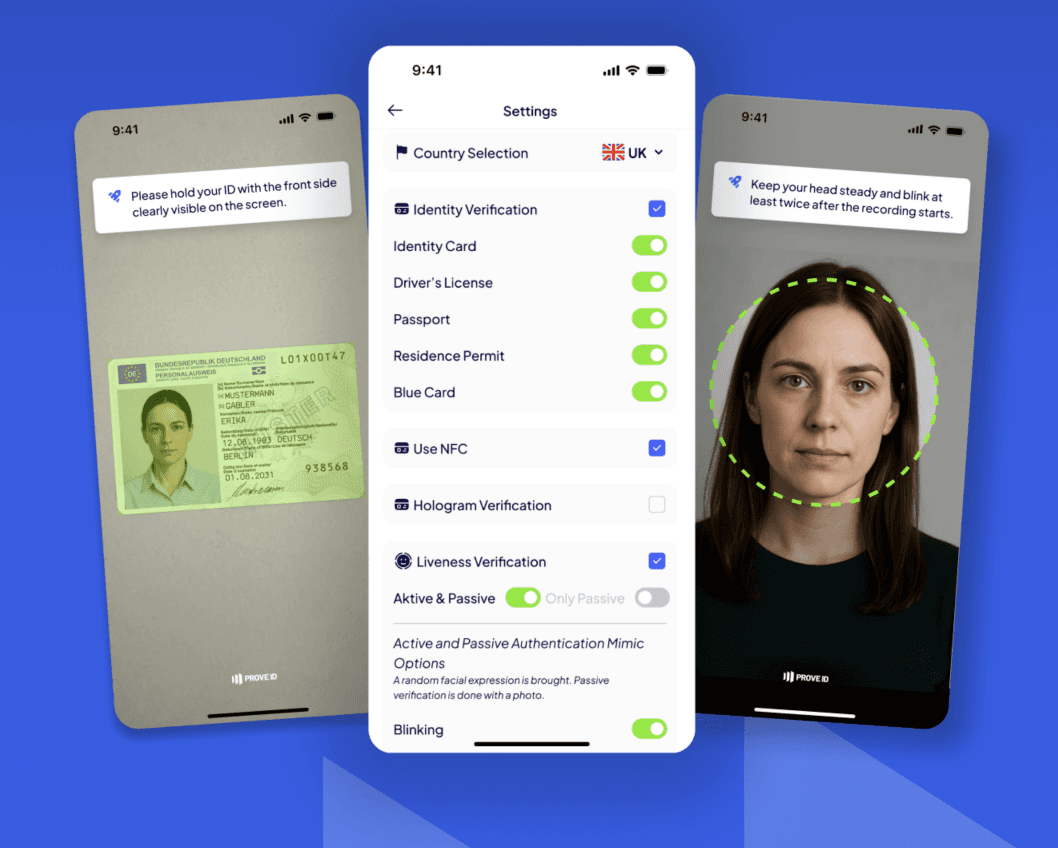
Otomatik Yüz Yakalama
Ekranda Birden Fazla Yüzü Tespit Etme
Yaş ve Cinsiyet Uyumu Tespiti
Yüz Tanıma
Automated Face Capture
Multi-Face Detection on Screen
Age and Gender Matching Analysis
Face Recognition
Expression Checks with Active Verification
Deepfake Screen Attack Detection
Voice-Based Verification Option
Liveness
Aktif Doğrulama ile İfade Kontrolleri
Deepfake Ekran Saldırısı Tespiti
Sesle Onay Seçeneği
Canlılık
Identifying customer pain points throughout the process Tracking attack attempts Real-time process performance monitoring
Advanced
Reporting
Müşterilerin süreçte yaşadığı zorlukları tespit
Saldırı girişimlerini takip
Gerçek zamanlı süreç performansını izleme olanakları
Gelişmiş Raporlama







NFC + OCR
On-device NFC reading with PACE key agreement and Chip Authentication (EAC).
Deep neural network–based AI model for OCR.
Cihaz üzerinde PACE anahtar anlaşması ve Çip Doğrulama (EAC) ile NFC okuma.
OCR için Derin Sinir Ağı tabanlı yapay zeka modeli.
Kimlik Kartında Bütünlük
Rainbow, Guilloché, Gizli Görsel, İmza Karakteri, Hologram, Photoshop Manipülasyonu ve 200’den fazla ek kontrol.
Full ID Card Integrity
Rainbow printing, Guilloché patterns, hidden images, signature character verification, hologram checks, Photoshop manipulation detection, and over 200 additional controls.
Hologram
Akıllı Cihaz İçi Kontrol: Kullanılamaz fotoğraf çekimini otomatik olarak engelleme ve kullanıcıyı en iyi açıyı bulması için yönlendirme
Smart on-device control: automatically preventing unusable photo capture and guiding users to find the optimal angle.

Otomatik Yüz Yakalama
Ekranda Birden Fazla Yüzü Tespit Etme
Yaş ve Cinsiyet Uyumu Tespiti
Yüz Tanıma
Automated Face Capture
Multi-Face Detection on Screen
Age and Gender Matching Analysis
Face Recognition
Expression Checks with Active Verification
Deepfake Screen Attack Detection
Voice-Based Verification Option
Liveness
Aktif Doğrulama ile İfade Kontrolleri
Deepfake Ekran Saldırısı Tespiti
Sesle Onay Seçeneği
Canlılık
Identifying customer pain points throughout the process Tracking attack attempts Real-time process performance monitoring
Advanced
Reporting
Müşterilerin süreçte yaşadığı zorlukları tespit
Saldırı girişimlerini takip
Gerçek zamanlı süreç performansını izleme olanakları
Gelişmiş Raporlama







NFC + OCR
On-device NFC reading with PACE key agreement and Chip Authentication (EAC).
Deep neural network–based AI model for OCR.
Cihaz üzerinde PACE anahtar anlaşması ve Çip Doğrulama (EAC) ile NFC okuma.
OCR için Derin Sinir Ağı tabanlı yapay zeka modeli.
Kimlik Kartında Bütünlük
Rainbow, Guilloché, Gizli Görsel, İmza Karakteri, Hologram, Photoshop Manipülasyonu ve 200’den fazla ek kontrol.
Full ID Card Integrity
Rainbow printing, Guilloché patterns, hidden images, signature character verification, hologram checks, Photoshop manipulation detection, and over 200 additional controls.
Hologram
Akıllı Cihaz İçi Kontrol: Kullanılamaz fotoğraf çekimini otomatik olarak engelleme ve kullanıcıyı en iyi açıyı bulması için yönlendirme
Smart on-device control: automatically preventing unusable photo capture and guiding users to find the optimal angle.

Otomatik Yüz Yakalama
Ekranda Birden Fazla Yüzü Tespit Etme
Yaş ve Cinsiyet Uyumu Tespiti
Yüz Tanıma
Automated Face Capture
Multi-Face Detection on Screen
Age and Gender Matching Analysis
Face Recognition
Expression Checks with Active Verification
Deepfake Screen Attack Detection
Voice-Based Verification Option
Liveness
Aktif Doğrulama ile İfade Kontrolleri
Deepfake Ekran Saldırısı Tespiti
Sesle Onay Seçeneği
Canlılık
Identifying customer pain points throughout the process Tracking attack attempts Real-time process performance monitoring
Advanced
Reporting
Müşterilerin süreçte yaşadığı zorlukları tespit
Saldırı girişimlerini takip
Gerçek zamanlı süreç performansını izleme olanakları
Gelişmiş Raporlama
Customers across different sectors
meet at Techsign technology.
Customers across different sectors
meet at Techsign technology.
“
“


As sahibinden.com, we confirm our customers' profiles with Techsign's highly secured KYC solutions.
Identity verification
LIVENESS TEST
HOLOGRAM
“
“


As pokus, we provide our customers a secure and user-friendly e-wallet experience with Techsign's end-to-end KYC solutions.
Identity verification
5 dıfferent ıd cards
lıveness
At Paratim, we offer tailored payment solutions for businesses while enabling individual users to manage all their financial transactions from a single app. With Techsign’s identity verification technology, we make our customer onboarding process more secure, cost-efficient, and fully compliant with regulations.
”
”
“
“



As sahibinden.com, we confirm our customers' profiles with Techsign's highly secured KYC solutions.
“
“
As pokus, we provide our customers a secure and user-friendly e-wallet experience with Techsign's end-to-end KYC solutions.
At Paratim, we offer tailored payment solutions for businesses while enabling individual users to manage all their financial transactions from a single app. With Techsign’s identity verification technology, we make our customer onboarding process more secure, cost-efficient, and fully compliant with regulations.
”
”
Supported by
Supported by
Supported by















“
“

As sahibinden.com, we confirm our customers' profiles with Techsign's highly secured KYC solutions.
Identity verification
LIVENESS TEST
HOLOGRAM
“
“

As pokus, we provide our customers a secure and user-friendly e-wallet experience with Techsign's end-to-end KYC solutions.
Identity verification
5 dıfferent ıd cards
lıveness

“
We have been using Techsign's biometric signature solution since 2019 in Ford Otosan branches in 8 different scenarios. With this technology, we support a more sustainable world and also improve our business processes
bıometrıc sıgnature
”
”
BLOG

Digital Signature Types
Not all digital signatures are the same. Learn the legal distinctions between electronic, advanced, and biometric signatures—and how Techsign’s compliant, white-label biometric solution simplifies secure, remote signing for modern businesses.

Reycan Çetin // Growth Manager @Techsign

Are Our Passwords Secure Enough? How Will Password Usage Change in the Future?
Weak passwords cause 30% of data breaches—and “123456” is still widely used. Learn why multi-factor and biometric authentication are the future, and how Techsign secures digital access with AI-powered, customizable identity solutions.

Barış Korkmaz

How Much Return Do KYC Solutions Provide? ROI Calculations
KYC & ID Verification solutions drive ROI by reducing costs, boosting productivity, and improving digital security. With Techsign’s AI-powered tools, businesses streamline customer onboarding, ensure compliance, and unlock new digital potential.

Mehmet Nuri Aybar // Senior Business Development Consultant
Incubation and Acceleration Programs That Can Help Startups
Incubators and accelerators guide startups from idea to growth, offering funding, mentorship, and more. Learn the key differences, top global programs, and Techsign’s own journey from early incubation to global acceleration success.

Reycan Çetin // Growth Manager @Techsign

Deepfake Threat in Identity Verification for Financial Systems
Deepfake tech is now a serious threat to financial systems, enabling fraudsters to bypass ID checks and liveness tests. Learn how attacks evolved—and how Techsign’s AI-powered security stays one step ahead of even the most advanced Deepfakes.

Reycan Çetin // Growth Manager @Techsign

What is Deepfake, why is it dangerous? How will we fight against the threats created by Deepfake?
Deepfake uses AI to alter real content—posing growing risks from identity fraud to political manipulation. Learn how it works, why the human eye fails to detect it, and how AI-driven defenses are our best hope to counter its evolving threats.

Osman S. Aktepe // Software Architect

Crypto Currencies, Security Problems, and Solutions
Crypto offers speed and flexibility—but also raises security concerns. Learn how Techsign’s AI-powered KYC tools, including face recognition and deepfake-resistant liveness checks, help crypto firms stay compliant and secure in a high-risk landscape.

Reycan Çetin // Growth Manager @Techsign
What is Pay-by-Face / Where Can It Be Used / How Does It Work?
Pay-by-face enables secure, fast, device-free payments using facial recognition. Learn how Techsign’s AI-driven system protects biometric data, prevents fraud, and reshapes user experience—without storing your actual face image.

Reycan Çetin // Growth Manager @Techsign

How Can Technology Help To Build Safer Micro Mobility Solutions?
Micro-mobility is rising—but safety and regulation must keep up. Discover how Techsign’s KYC tools like OCR, face recognition, and age verification can help cities and scooter firms create safer, smarter, and more inclusive transport systems.

Reycan Çetin // Growth Manager @Techsign
The Difference Between AML and KYC: Understanding Two Vital Components of Financial Security
AML and KYC are vital to financial security—while KYC verifies identity, AML prevents money laundering. Learn how Techsign’s AI-powered, legally compliant KYC solutions simplify remote onboarding with secure document and biometric verification.

Reycan Çetin // Growth Manager @Techsign

Should KYC Processes be Solved with Your Own Resources or Outsourced?
Should you build your own KYC system or work with a trusted provider? Discover the pros and cons of each path—and how Techsign’s expert solutions can reduce risk, save time, and ensure compliance in today’s fast-moving digital landscape.

Barış Korkmaz

How to Do KYC Verification? How Does KYC Work?
KYC is no longer just for banks—it's now vital in sectors from healthcare to gaming. As digital onboarding grows, AI-powered KYC ensures secure, compliant, and seamless user experiences across industries. Discover where it’s heading next.

Reycan Çetin // Growth Manager @Techsign

Identity Verification Methods - 5 Different Methods
Biometric authentication is rising—but no method is flawless alone. Learn why multi-factor authentication is essential, how each method compares, and how Techsign combines AI-powered biometrics with layered security for reliable identity verification.

AI Agents in Remote Know Your Customer
Video calls once secured remote onboarding—but deepfakes and high costs changed the game. Discover how Techsign’s AI agents offer faster, safer, and more scalable identity verification, detecting fraud beyond what the human eye can catch.

Reycan Çetin // Growth Manager @Techsign
Confusing Deepfake Examples from 2023 and 2024
From fake Elon Musk speeches to Tom Cruise TikToks, deepfakes are more realistic—and risky—than ever. Explore recent examples, the dangers they pose, and how tools like Techsign’s Fake Finder help uncover what’s real and what’s not.

Reycan Çetin // Growth Manager @Techsign

Quantum-Resistant Cryptography in Identity Verification
Quantum computing could break today’s encryption—but quantum-resistant cryptography offers hope. Explore why securing digital identities now is key, and how the tech world is preparing for a future where quantum threats are real.

Serkan Fergan

Differences Between Cheapfake and Deepfake and the Threats They Pose in Identity Fraud
Cheapfakes and deepfakes both threaten identity systems—but in different ways. Learn the key differences, how each is used in fraud, and why Techsign’s AI-powered liveness detection and multi-factor tools are essential for digital security.

Reycan Çetin // Growth Manager @Techsign

Fraud as a Service (FaaS): Committing Fraud Has Never Been This Easy!
Fraud is now a service—sold with tools, support, and guides to anyone online. Learn how FaaS is reshaping cybercrime and how Techsign’s AI-powered, risk-based authentication helps businesses stay protected in this new era of digital fraud.

Reycan Çetin // Growth Manager @Techsign

Deepfake Scams: A New Threat in the Digital World
Deepfake scams are on the rise—from romance fraud to KYC bypass attempts. Learn how scammers exploit AI to deceive individuals and institutions, and how Techsign’s detection tools help uncover fake content before it’s too late.

Reycan Çetin // Growth Manager @Techsign

Digital Signature Types
Not all digital signatures are the same. Learn the legal distinctions between electronic, advanced, and biometric signatures—and how Techsign’s compliant, white-label biometric solution simplifies secure, remote signing for modern businesses.

Reycan Çetin // Growth Manager @Techsign

Are Our Passwords Secure Enough? How Will Password Usage Change in the Future?
Weak passwords cause 30% of data breaches—and “123456” is still widely used. Learn why multi-factor and biometric authentication are the future, and how Techsign secures digital access with AI-powered, customizable identity solutions.

Barış Korkmaz

How Much Return Do KYC Solutions Provide? ROI Calculations
KYC & ID Verification solutions drive ROI by reducing costs, boosting productivity, and improving digital security. With Techsign’s AI-powered tools, businesses streamline customer onboarding, ensure compliance, and unlock new digital potential.

Mehmet Nuri Aybar // Senior Business Development Consultant

Incubation and Acceleration Programs That Can Help Startups
Incubators and accelerators guide startups from idea to growth, offering funding, mentorship, and more. Learn the key differences, top global programs, and Techsign’s own journey from early incubation to global acceleration success.

Reycan Çetin // Growth Manager @Techsign

Digital Signature Types
Not all digital signatures are the same. Learn the legal distinctions between electronic, advanced, and biometric signatures—and how Techsign’s compliant, white-label biometric solution simplifies secure, remote signing for modern businesses.

Reycan Çetin // Growth Manager @Techsign

Are Our Passwords Secure Enough? How Will Password Usage Change in the Future?
Weak passwords cause 30% of data breaches—and “123456” is still widely used. Learn why multi-factor and biometric authentication are the future, and how Techsign secures digital access with AI-powered, customizable identity solutions.

Barış Korkmaz

How Much Return Do KYC Solutions Provide? ROI Calculations
KYC & ID Verification solutions drive ROI by reducing costs, boosting productivity, and improving digital security. With Techsign’s AI-powered tools, businesses streamline customer onboarding, ensure compliance, and unlock new digital potential.

Mehmet Nuri Aybar // Senior Business Development Consultant

Incubation and Acceleration Programs That Can Help Startups
Incubators and accelerators guide startups from idea to growth, offering funding, mentorship, and more. Learn the key differences, top global programs, and Techsign’s own journey from early incubation to global acceleration success.

Reycan Çetin // Growth Manager @Techsign
Teknopark No:1/1C, Office: 1301 34906
İstanbul/Türkiye
t. +90 (216) 510 2761
m. info@techsign.com
Let’s connect and build
the solution you need!
Teknopark No:1/1C, Ofis: 1301 34906 İstanbul/Türkiyet. +90 (216) 510 2761m. info@techsign.com
İhtiyacınıza en uygun çözümü
gelin, birlikte keşfedelim.
Copyright 2025 © Techsign
Teknopark No:1/1C, Office: 1301 34906
İstanbul/Türkiye
t. +90 (216) 510 2761
m. info@techsign.com
Let’s connect and build
the solution you need!
Teknopark No:1/1C, Ofis: 1301 34906 İstanbul/Türkiyet. +90 (216) 510 2761m. info@techsign.com
İhtiyacınıza en uygun çözümü
gelin, birlikte keşfedelim.
Copyright 2025 © Techsign
Teknopark No:1/1C, Office: 1301 34906
İstanbul/Türkiye
t. +90 (216) 510 2761
m. info@techsign.com
Let’s connect and build
the solution you need!
Teknopark No:1/1C, Ofis: 1301 34906 İstanbul/Türkiyet. +90 (216) 510 2761m. info@techsign.com
İhtiyacınıza en uygun çözümü
gelin, birlikte keşfedelim.
Copyright 2025 © Techsign
